Navigating The Cyber Threat Landscape: A Comprehensive Guide To Cybersecurity Threat Maps
Navigating the Cyber Threat Landscape: A Comprehensive Guide to Cybersecurity Threat Maps
Related Articles: Navigating the Cyber Threat Landscape: A Comprehensive Guide to Cybersecurity Threat Maps
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Navigating the Cyber Threat Landscape: A Comprehensive Guide to Cybersecurity Threat Maps. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Cyber Threat Landscape: A Comprehensive Guide to Cybersecurity Threat Maps
In today’s interconnected world, cybersecurity threats are constantly evolving, becoming more sophisticated and pervasive. Organizations of all sizes face a daunting task: understanding and mitigating the ever-present risks to their digital infrastructure and sensitive data. This is where cybersecurity threat maps emerge as invaluable tools, providing a visual and insightful representation of the complex landscape of threats, vulnerabilities, and potential attack vectors.
Understanding the Concept: Visualizing the Cyber Threat Landscape
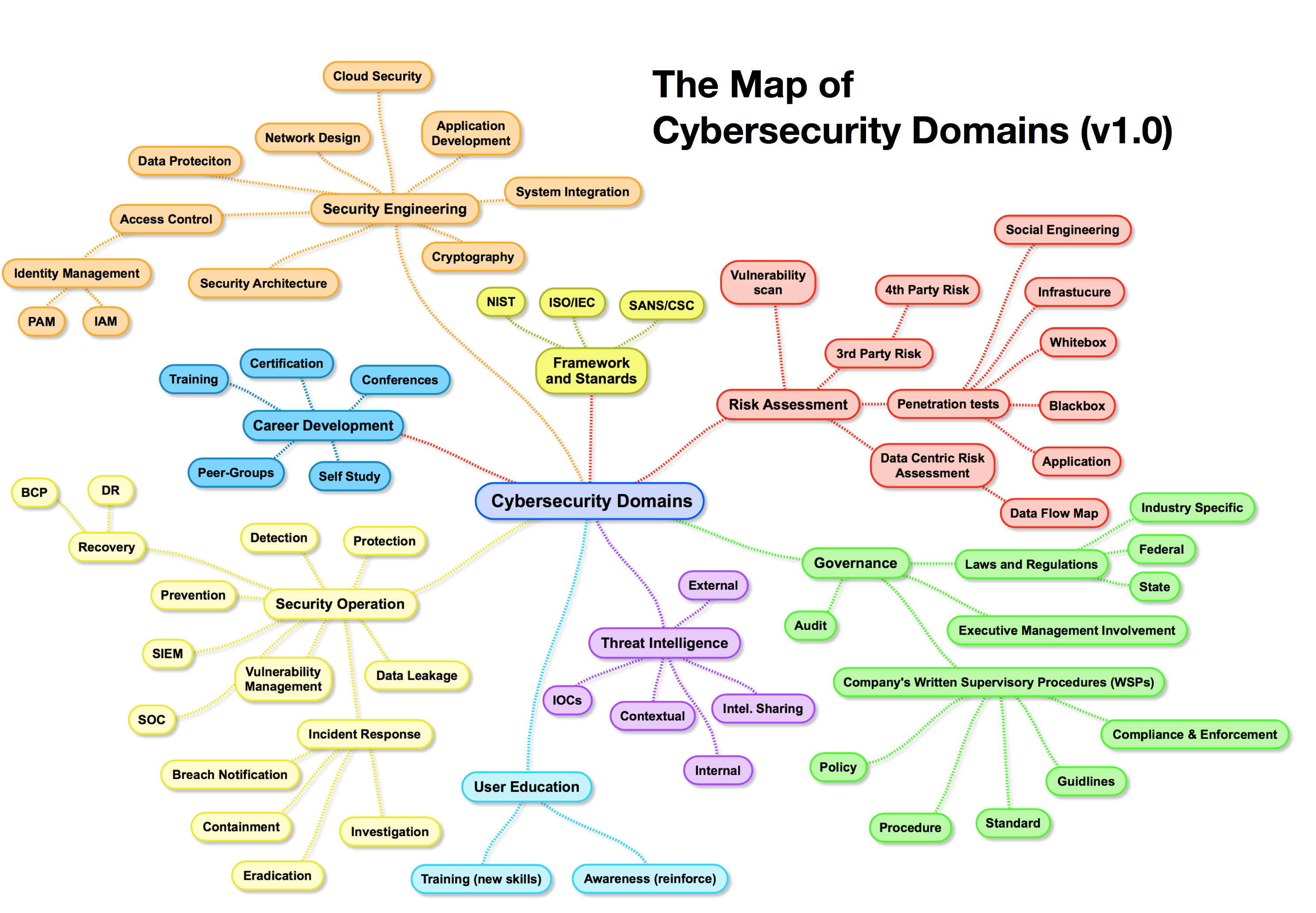
A cybersecurity threat map is a graphical representation of potential threats, vulnerabilities, and attack vectors that an organization may face. It provides a holistic view of the cyber threat landscape, offering insights into the types of threats, their origins, potential targets, and the most likely attack methods. These maps can be customized to reflect the specific vulnerabilities and risks associated with an organization’s unique infrastructure, industry, and geographical location.
Components of a Comprehensive Cybersecurity Threat Map
A well-structured cybersecurity threat map typically includes the following components:
- Threat Actors: These are the individuals or groups responsible for carrying out cyberattacks. The map identifies the motivations, capabilities, and tactics of various threat actors, including state-sponsored actors, criminal organizations, hacktivists, and individuals.
- Attack Vectors: This element highlights the pathways through which attackers can exploit vulnerabilities and gain access to systems. Examples include phishing emails, malicious websites, compromised software, and network intrusions.
- Vulnerabilities: These are weaknesses in systems, applications, or configurations that can be exploited by attackers. The map identifies known vulnerabilities, including those related to operating systems, software applications, network devices, and user practices.
- Impact: This component assesses the potential consequences of a successful cyberattack, including data breaches, system downtime, financial losses, reputational damage, and legal liabilities.
- Mitigation Strategies: The map outlines recommended countermeasures and best practices to address identified threats and vulnerabilities. These strategies may include security controls, risk assessments, incident response plans, and employee training programs.
Benefits of Utilizing Cybersecurity Threat Maps
The strategic use of cybersecurity threat maps offers a multitude of benefits for organizations, enabling them to:
- Gain a Comprehensive Understanding of Threats: Maps provide a clear and concise overview of the cyber threat landscape, helping organizations identify and prioritize the most significant risks.
- Proactive Risk Management: By identifying vulnerabilities and potential attack vectors, organizations can take proactive steps to mitigate risks and strengthen their defenses.
- Effective Resource Allocation: Threat maps help organizations allocate resources efficiently, focusing on the most critical vulnerabilities and threats.
- Improved Incident Response: By understanding the threat landscape and potential attack methods, organizations can develop more effective incident response plans and strategies.
- Enhanced Security Awareness: Threat maps can be used to raise security awareness among employees, promoting best practices and encouraging responsible online behavior.
- Data-Driven Decision Making: Threat maps provide valuable data that supports informed decision-making regarding security investments, risk assessments, and strategic planning.
Types of Cybersecurity Threat Maps
Cybersecurity threat maps can be categorized based on their scope, purpose, and target audience. Common types include:
- Industry-Specific Threat Maps: These maps focus on the specific threats and vulnerabilities faced by organizations within a particular industry, such as healthcare, finance, or retail.
- Regional Threat Maps: These maps provide insights into the cyber threats prevalent in specific geographical regions, taking into account regional geopolitical factors and cybercrime trends.
- Organization-Specific Threat Maps: These maps are tailored to the unique infrastructure, systems, and data of a specific organization, providing a customized view of its cyber risks.
- Threat Intelligence Platforms: These advanced platforms integrate threat data from various sources, providing real-time insights into emerging threats and attack patterns.
FAQs on Cybersecurity Threat Maps
1. How are cybersecurity threat maps created?
Threat maps are typically developed through a collaborative process involving security professionals, analysts, and stakeholders. The process involves:
- Data Gathering: Collecting data from various sources, including industry reports, threat intelligence feeds, vulnerability databases, and internal security assessments.
- Threat Analysis: Analyzing the collected data to identify the most significant threats, vulnerabilities, and attack vectors.
- Visualization: Representing the identified threats and vulnerabilities graphically using tools like mapping software, dashboards, or interactive visualizations.
- Regular Updates: Maintaining the map by continuously monitoring for new threats, vulnerabilities, and changes in the cyber threat landscape.
2. What are the limitations of cybersecurity threat maps?
While powerful tools, threat maps have limitations:
- Data Accuracy: The accuracy of the map depends on the quality and completeness of the data used.
- Dynamic Nature of Threats: The cyber threat landscape is constantly evolving, so threat maps require regular updates to remain relevant.
- Complexity: Creating and maintaining comprehensive threat maps can be complex, requiring specialized expertise and resources.
- Bias: Threat maps may reflect biases based on the sources of data used or the perspectives of the individuals involved in their creation.
3. How can organizations use cybersecurity threat maps effectively?
To maximize the benefits of threat maps, organizations should:
- Involve Key Stakeholders: Engage security professionals, IT teams, business leaders, and relevant departments in the map development and usage process.
- Regularly Review and Update: Continuously monitor for new threats and vulnerabilities, updating the map accordingly.
- Integrate with Other Security Tools: Connect the threat map with other security tools, such as vulnerability scanners, intrusion detection systems, and security information and event management (SIEM) platforms.
- Communicate Effectively: Share insights from the threat map with relevant stakeholders, promoting security awareness and collaboration.
Tips for Creating and Utilizing Cybersecurity Threat Maps
- Focus on Relevance: Prioritize threats and vulnerabilities that are most likely to impact your organization.
- Use Clear and Concise Visualizations: Employ clear and intuitive graphics to make the map easy to understand and interpret.
- Integrate Threat Intelligence: Leverage external threat intelligence feeds to enhance the accuracy and relevance of the map.
- Establish a Review and Update Schedule: Regularly review and update the map to reflect changes in the cyber threat landscape.
- Consider User Needs: Tailor the map to the needs and understanding of different stakeholders, including technical and non-technical audiences.
Conclusion: Navigating the Cyber Threat Landscape with Confidence
Cybersecurity threat maps are indispensable tools for organizations seeking to understand and mitigate the risks posed by the constantly evolving cyber threat landscape. By providing a visual representation of potential threats, vulnerabilities, and attack vectors, these maps empower organizations to make informed security decisions, prioritize resources, and enhance their overall cybersecurity posture. As the cyber threat landscape continues to evolve, the use of threat maps will become increasingly crucial for organizations seeking to protect their digital assets and ensure their continued operations.
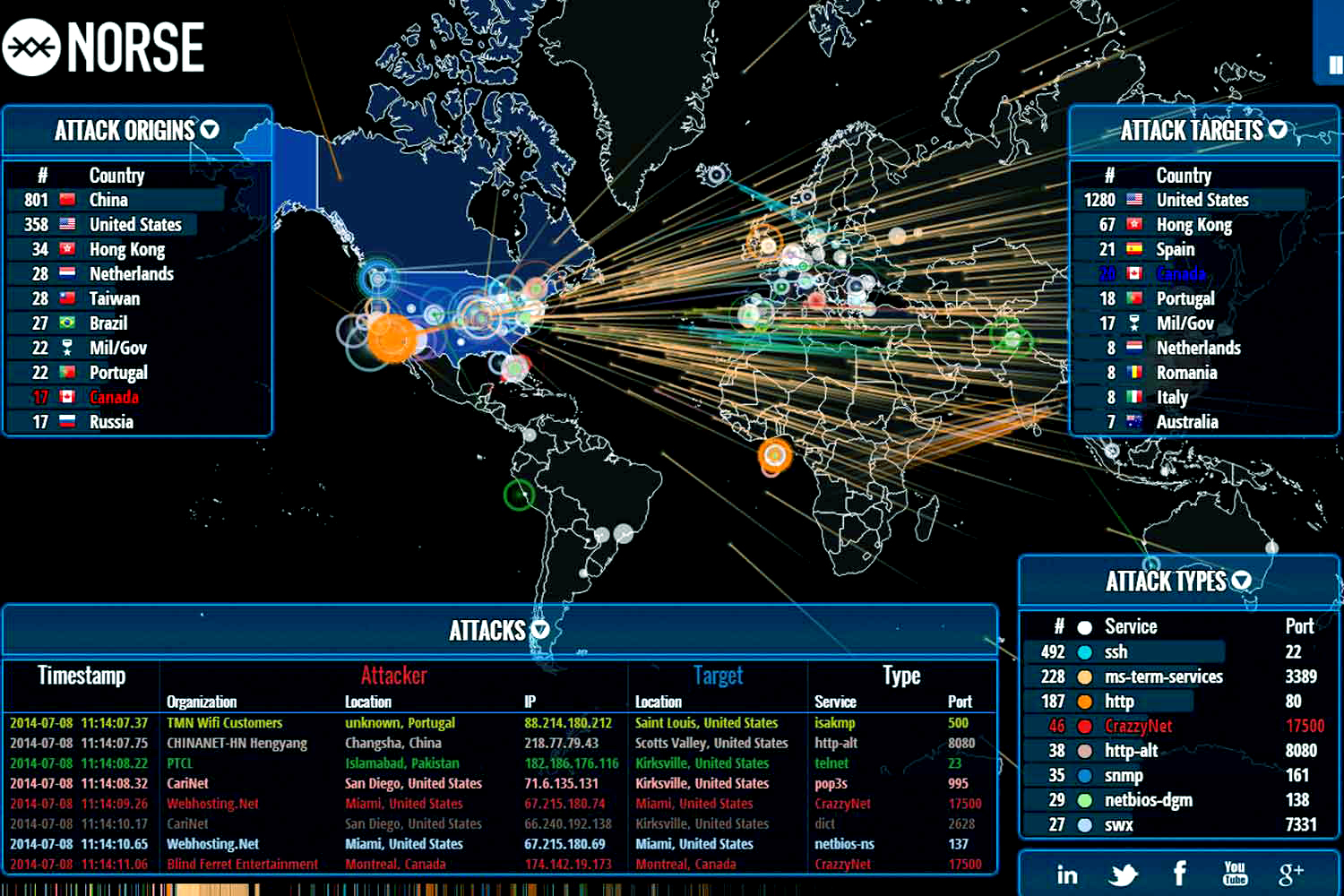



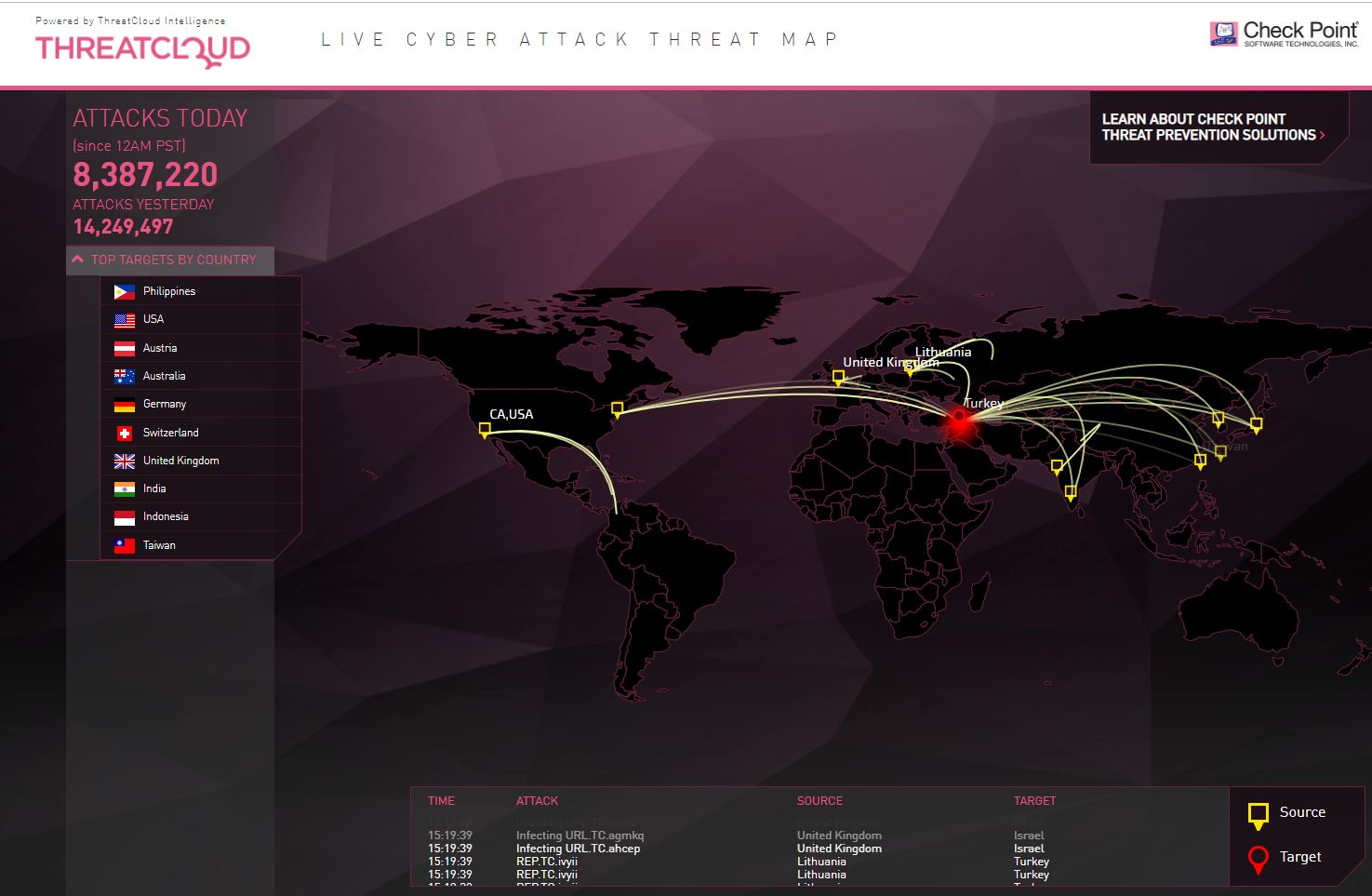

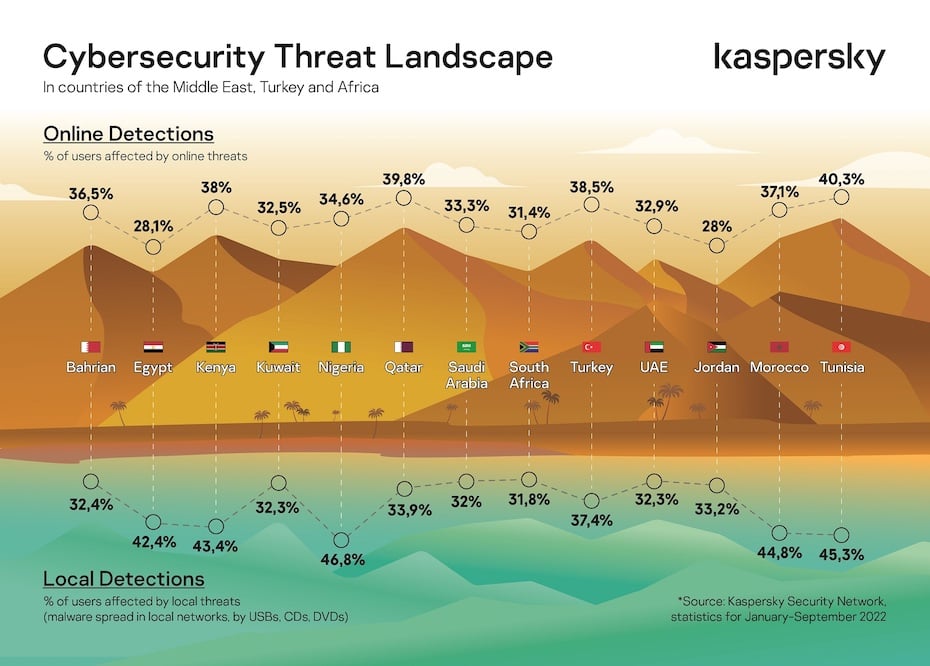

Closure
Thus, we hope this article has provided valuable insights into Navigating the Cyber Threat Landscape: A Comprehensive Guide to Cybersecurity Threat Maps. We thank you for taking the time to read this article. See you in our next article!
You may also like
Recent Posts
- Navigating The Digital Landscape: A Comprehensive Guide To AT&T’s Service Map For Internet
- Navigating The Keystone Resort Ski Map: A Comprehensive Guide To Exploring The Mountain
- Navigating The Waters: Understanding Nautical Mile Maps
- Navigating The Rails: A Comprehensive Guide To The RTD Train Map
- Navigating Baltimore County: A Guide To The Zoning Map
- A Comprehensive Guide To Parris Island, South Carolina: Navigating The Cradle Of Marines
- Navigating The Waters Of Smith Lake, Alabama: A Comprehensive Guide
- Navigating Kingsland, Texas: A Comprehensive Guide To The City’s Map
Leave a Reply